Individual verifiability of the vote
This article explains how to verify your own vote in a secure and anonymous way.
The individual verifiability function, if enabled, allows voters to check that each vote cast has been correctly and immutably recorded in the system.
To do this, Eligo generates a hash for each voter, which is a unique encrypted code representing the voting receipt.
The voting process does not change, but verifiability adds an additional step aimed at improving the security, transparency, and auditability of the entire voting process.
Administrator-side verifiability
1. Access to the Bulletin Board
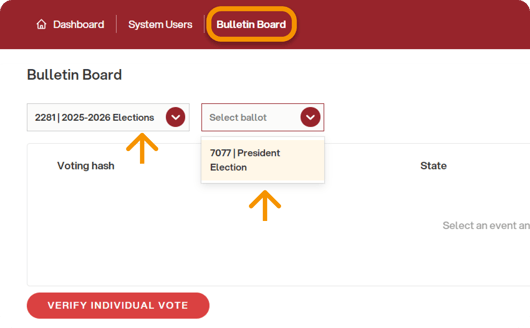
From the back-office menu, the item “BULLETIN BOARD” will be visible, showing the voting hashes for each ballot.
After creating and opening an electoral event, select the event and the ballot from the dropdown menu:
2. View of real-time hashes
As voters cast their votes, a table will appear showing the list of generated hashes:
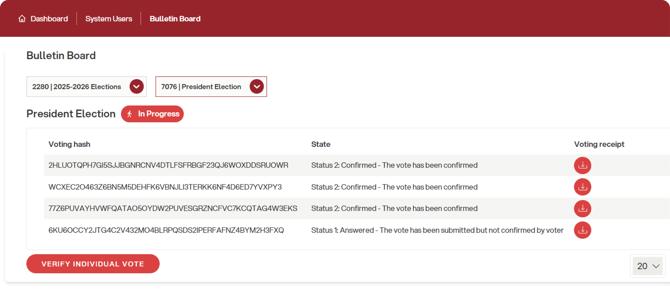
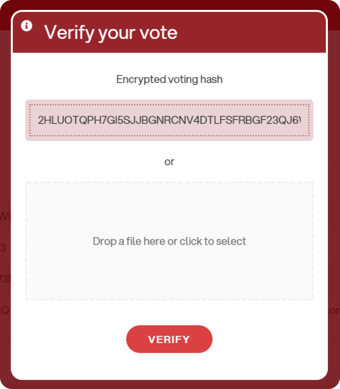
It will be possible to download the receipt for each vote, either by copying the hash or by downloading a file in .json format. Afterwards, you can verify the individual vote by clicking the appropriate button and then pasting the string or dragging the .json file into the designated box:
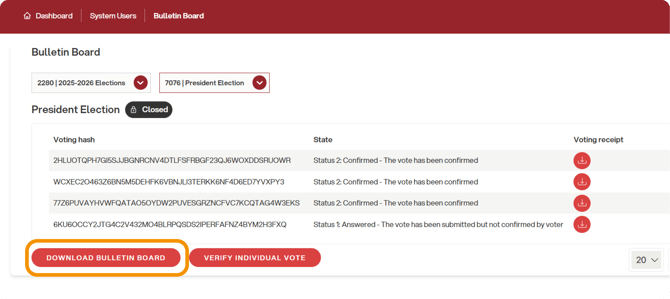
Once voting is closed, the administrator can continue to access the Bulletin Board and may also download a .json file containing all submitted receipts and perform a universal vote verifiability check.
Voter-Side verifiability
1. Receiving the hash
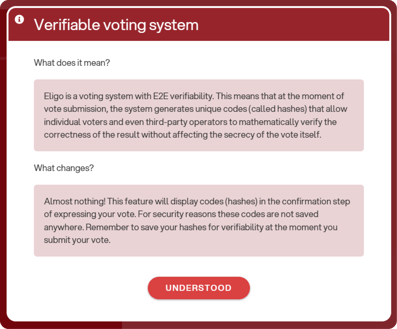
At login, an informational pop-up will appear notifying the voter that vote verifiability is enabled. Simply click “Understood”:
When the vote is confirmed, the encrypted voting receipt (the vote hash) will be provided.
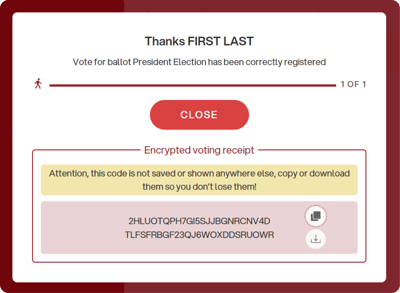
The code can be copied or downloaded as a .json file.
⚠️ If the voter does not save the hash at this moment, it cannot be retrieved later.
Administrators see only the list of hashes, but cannot associate them with individual users.
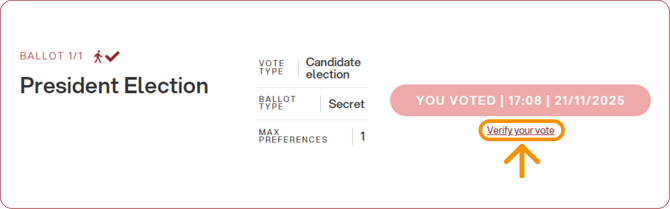
2. Verifying your own vote
To verify their vote, the voter clicks the appropriate button:
They can then paste the hash or drag the file into the box. Next, click “Verify”:
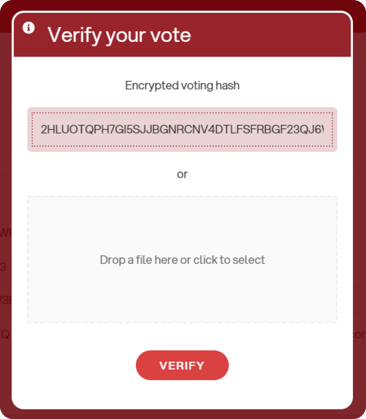
If the code entered is correct, a confirmation will appear indicating that the vote has been correctly placed into the digital ballot box:
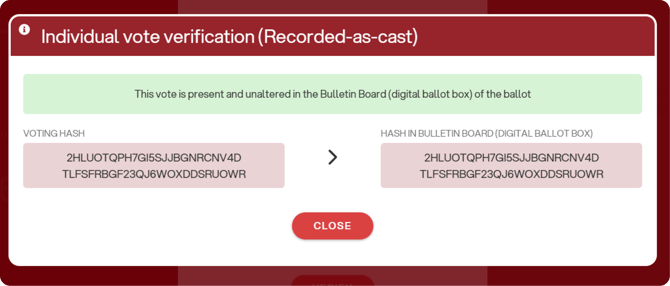
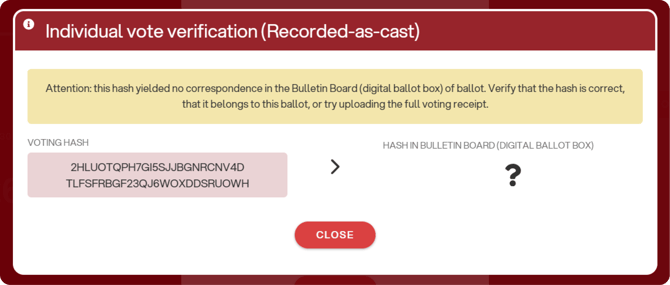
If the hash does not match, an error message will be shown:
Privacy considerations
The hash contains no personal data and does not allow anyone to trace back the voter’s choice. Its presence does not compromise ballot secrecy because it represents only an encrypted receipt with no identifying references.
When the voter downloads the encrypted file, it includes the event ID, ballot ID, and their username, allowing them to keep their own receipt.
The administrator, however, has access only to a version of the file that contains the event ID and ballot ID, with no data that could link a hash to a specific user.